
The investigation carried out by a consortium of security companies, who have spent several years investigating Lázaro's activities, associate the group with a hacktivist profile (hackers attacking entities that ethics have been questioned) but curiously after Investigations have ensured that more than 60% of the malware related to the Lazarus it has analyzed contains the texts in Korean, placing on the track the political motivations between South Korea and the United States.
What happened?
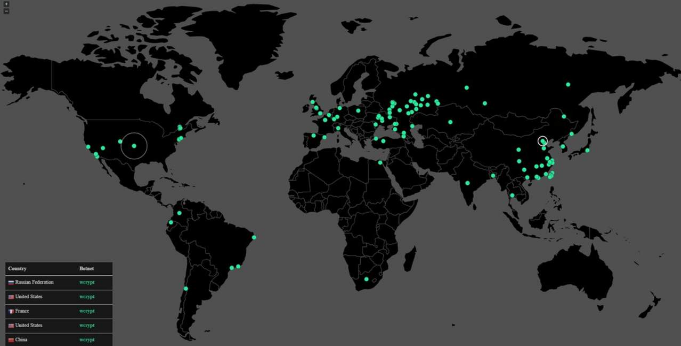
May 12, 2017, a global cyberattack with the WannaCry virus was generated, leaving about 200,000 victims in less than 150 countries. This virus WannaCry is a piece of software that hijacks the files of a computer and then request its rescue to the users a change of a sum of money. Several companies, hospitals and other governmental entities have partially or totally paralyzed their operations after being infected.
What is a ransomware virus?
It is a malicious module whose main function is to encrypt the files of our Windows system with strong cryptography.
Asymmetric Cryptography
Also called public key cryptography is a cryptographic method that uses a key pair for sending messages. Both keys belong to the same person who sent the message. Cryptographic methods ensure that this pair of keys can only be generated once, so it can be assumed that it is not possible for two people to have casually obtained the same pair of keys. If the sender uses the public key of the recipient to encrypt the message, once encrypted, only the private key of the recipient can decrypt this message, since it is the only one that knows it. Therefore the confidentiality of sending the message is achieved, no one but the recipient can decipher it. If the owner of the key pair uses their private key to encrypt the message, anyone can decrypt it using their public key. In this case it is possible to identify and authenticate the sender, since it is known that he could only have used his private key (unless someone had been able to steal it). This idea is the foundation of electronic signatures.

How important is this process to be done with strong cryptography?
This allows that if you don't have the (private) decryption key, it is not possible by any other means recover the original files.
What does the cybercriminal need to be able to attack?
Social engineering, get a list of contacts to attack and hire a service that sends malicious mail.
How infection occurs?
Usually occurs when receiving by e-mail or other digital means, an encrypted program, pretending to be something else, that when executed decrypts the harmful code and encrypts our files.
How are these viruses transmitted?
These viruses search through the network for all available drives and encrypt all files of certain types (documents, spreadsheets, databases, etc.) ensuring that the system remains in operation, although they sometimes leave it locked with the infection notification screen.
What do the creators of the virus ask for?
They ask for a payment in bitcoins, that being a digital currency is very difficult to trace. The funny thing is that this time it has demanded the payment of 300 $ for the equipment and if this payment is delayed 3 days more, they raise the price of rescue.
Why it happened?
The attack takes advantage of a security vulnerability documented by Microsoft in MS17-010, released March 17, 2017. This vulnerability affects computers that do not have the latest security updates.
How did it happen?
The infection started with an email (phishing).
"The anonymous hero"
This is called the British cybersecurity researcher Marcus Hutchins, 22, who has managed to stop the threat of WannaCry.

How did the attack stop?
Although it was not possible to stop the infection altogether, the attack stopped. With the help of Darien Huss, from Proofpoint, they have found a "red switch" (kill switch) on the ransomware that stops it. This is an unregistered web address to which the malware made a request to this http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Therefore, if WannaCry does not get response from that web, it expands. If activated, it stops. In this way, Marcus bought a domain that was free and redirected the traffic that generated the virus to a server hosted in Los Angeles.
Lazarus probably provoked the WannaCry cyber attack
The international corporation that develops computer software, Symantec, estimated that ransomware presented several characteristics to the attack by Lazarus against Sony Pictures in 2014. Without evoking alleged links between the group and North Korea, Symantec explained that an earlier version of WannaCry was used in a small number of attacks three months before the global cyber attack.
In response to this Pyongyang denied any relation to this massive computer attack that infected hundreds of thousands of computers in the world.
Creating a Ransomware with Python
In this tutorial you can learn how to create a ramsonware with python.